Moodle is a Course Management System (CMS), also known as a Learning Management System (LMS) or a Virtual Learning Environment (VLE). It is a free web application that educators can use to create effective online/offline learning sites.
In this article, let us learn to build a LMS site with Moodle on CentOS 6.x. Here x stands for version such as 6.1, 6.2 etc. My testbox hostname and IP address are server.unixmen.com and 192.168.1.200/24 respectively.
Prerequisites
You should install and configure a LAMP server first. Moodle needs the following PHP extensions to run properly.
[root@server ~]# yum install php-iconv php-mbstring php-curl php-openssl php-tokenizer php-xmlpc php-soap php-ctype php-zip php-gd php-simplexml php-spl php-pcre php-dom php-xml php-intl php-json php-ldap php-pecl-apc -y
PHP settings
Open up /etc/php.ini file and make sure that you have configured the settings as shown below:
[root@server ~]# vi /etc/php.ini
register_globals = Off
safe_mode = Off
memory_limit = 128M
session.save_handler = files
magic_quotes_gpc = Off
magic_quotes_runtime = Off
file_uploads = On
session.auto_start = 0
session.bug_compat_warn = Off
post_max_size = 100M
upload_max_filesize = 100M
Restart your web server:
[root@server ~]# service httpd restart
Create MySQL database and user for Moodle
Here I create a database ‘moodledb’ and a user ‘moodleadmin’ with password ‘centos’:
[root@server ~]# mysql -u root -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 1
Server version: 5.5.31-MariaDB MariaDB Server
Copyright (c) 2000, 2013, Oracle, Monty Program Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> create database moodledb;
Query OK, 1 row affected (0.04 sec)
MariaDB [(none)]> GRANT ALL PRIVILEGES ON moodledb.* TO 'moodleadmin' IDENTIFIED BY 'centos';
Query OK, 0 rows affected (0.03 sec)
MariaDB [(none)]> flush privileges;
Query OK, 0 rows affected (0.01 sec)
MariaDB [(none)]> exit
Bye
Install Moodle
Download the latest version from here. Or you can directly download from the terminal using the following command:
[root@server ~]# wget http://download.moodle.org/download.php/direct/stable25/moodle-latest-25.zip
Extract the downloaded zip file:
[root@server ~]# unzip moodle-latest-25.zip
This will create a new directory called moodle in your current directory. Copy all the contents of moodle to your website root document folder.
If your server is dedicated to host only moodle site, copy the contents of your moodle directory to /var/www/html/ directory. In this case your moodle website URL will be www.your-site.com.
If your server is shared server, copy the contents of moodle directory to /var/www/html/moodle/. In this case your moodle website URL will be www.your-site.com/moodle.
Here I use a sub directory to host my moodle site. So the command should be:
[root@server ~]# cp -fr moodle/ /var/www/html/moodle
Set the following permissions for root user to moodle directory:
[root@server ~]# chown -R root /var/www/html/moodle/
[root@server ~]# chmod -R 755 /var/www/html/moodle/
Create data directory for Moodle
Moodle requires a directory to store all of its files (all your site’s uploaded files, temporary data, session data etc.). The web server needs to be able to write to this directory. On larger systems consider how much free space you are going to use when allocating this directory.
IMPORTANT: This directory must NOT be accessible directly via the web. This would be a serious security hole. Do not try to place it inside your web root or inside your Moodle program files directory. Moodle will not install. It can go anywhere else convenient.
[root@server ~]# mkdir /var/www/moodledata/
[root@server ~]# chmod 777 /var/www/moodledata/
Begin Moodle installation
Open up your web browser and navigate to http://ip-address/ if you copied the moodle directory contents to Apache document root folder or http://ip-address/moodle if you copied the moodle directory contents to a sub directory of Apache root.
Choose your desired language and press Next.
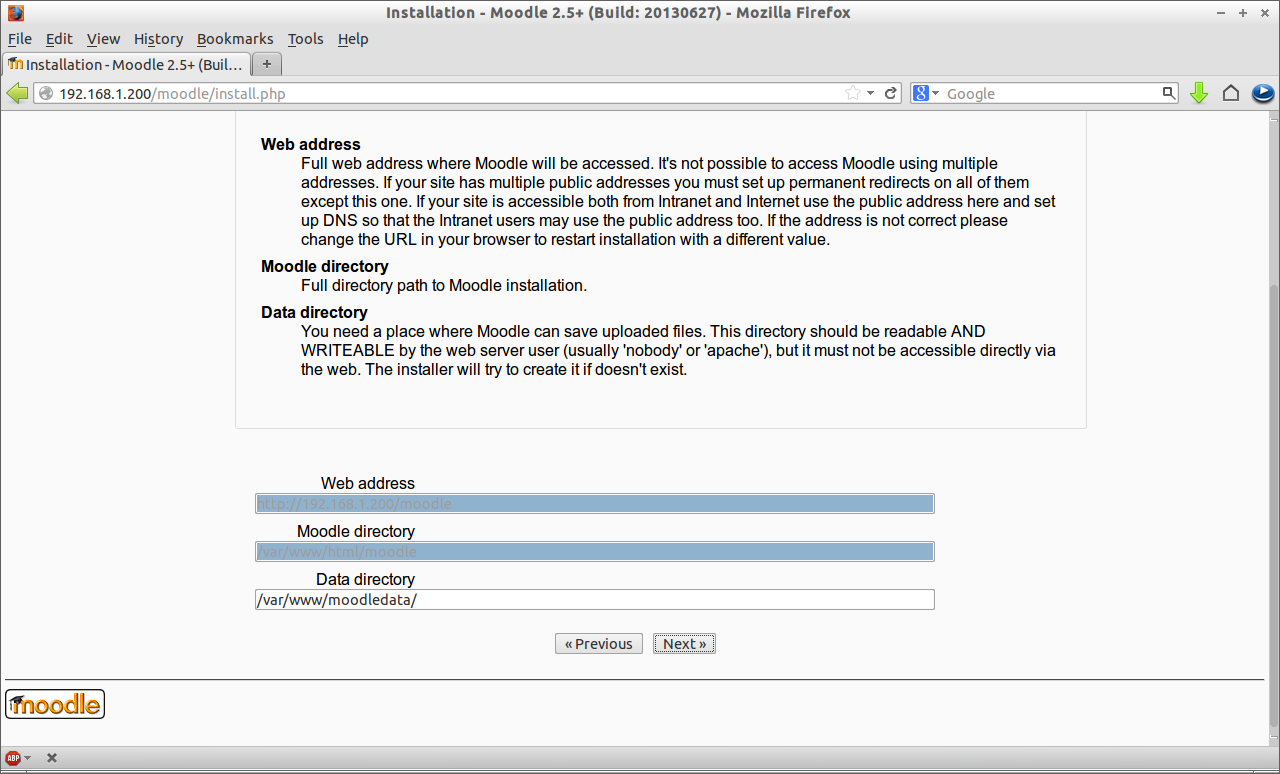
![Installation - Moodle 2.5+ (Build: 20130627) - Mozilla Firefox_001]() Enter Moodle data directory path and press Next.
Enter Moodle data directory path and press Next.
![Installation - Moodle 2.5+ (Build: 20130627) - Mozilla Firefox_003]() Select the database driver. In my case it’s mysql. Press Next.
Select the database driver. In my case it’s mysql. Press Next.
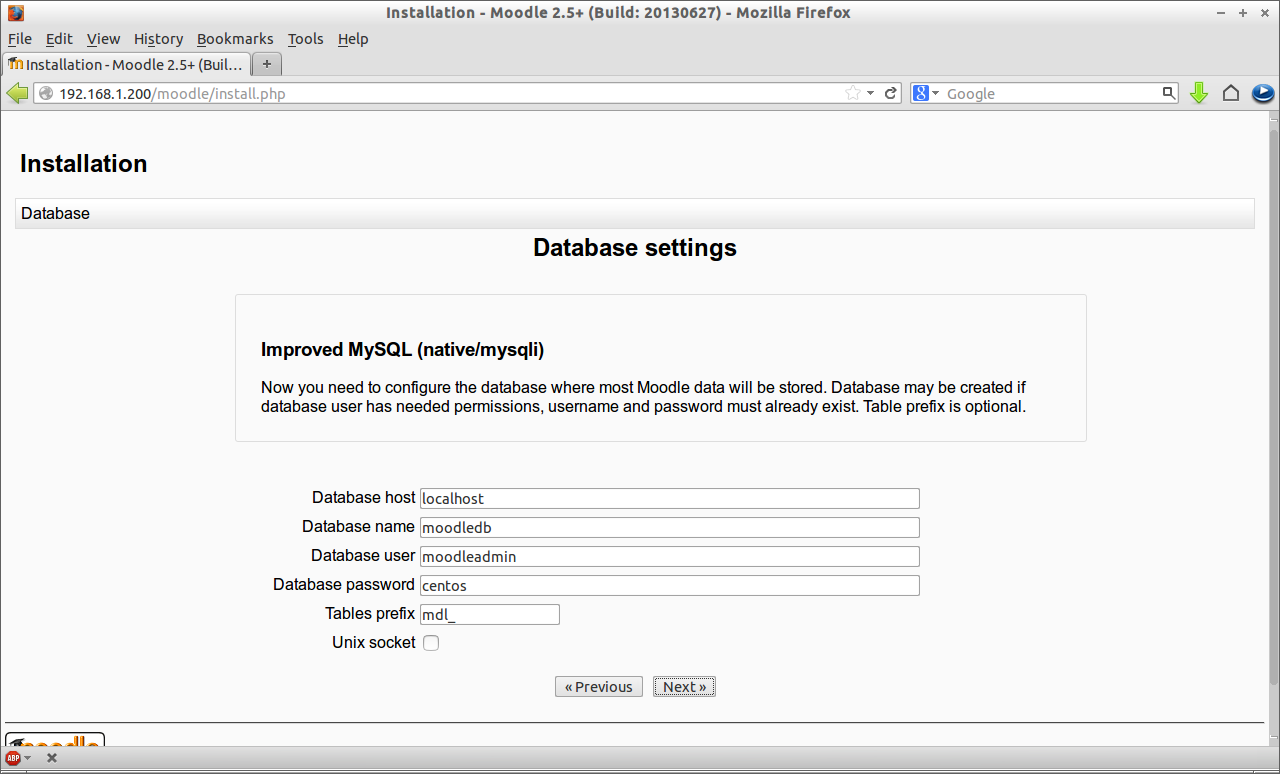
![Installation - Moodle 2.5+ (Build: 20130627) - Mozilla Firefox_004]() Enter database name and database user details and press Next.
Enter database name and database user details and press Next.
![Installation - Moodle 2.5+ (Build: 20130627) - Mozilla Firefox_005]() You will be asked to save the settings. The installer will ask you to create a config.php file in your moodle root folder with the contents of below output.
You will be asked to save the settings. The installer will ask you to create a config.php file in your moodle root folder with the contents of below output.
![Installation - Moodle 2.5+ (Build: 20130627) - Mozilla Firefox_006]() So let us create a config.php file with following command:
So let us create a config.php file with following command:
[root@server ~]# vi /var/www/html/moodle/config.php
Add the lines from the above output as shown below:
<?php // Moodle configuration file
unset($CFG);
global $CFG;
$CFG = new stdClass();
$CFG->dbtype = 'mysqli';
$CFG->dblibrary = 'native';
$CFG->dbhost = 'localhost';
$CFG->dbname = 'moodledb';
$CFG->dbuser = 'moodleadmin';
$CFG->dbpass = 'centos';
$CFG->prefix = 'mdl_';
$CFG->dboptions = array (
'dbpersist' => 0,
'dbsocket' => 0,
);
$CFG->wwwroot = 'http://192.168.1.200/moodle';
$CFG->dataroot = '/var/www/moodledata/';
$CFG->admin = 'admin';
$CFG->directorypermissions = 0777;
require_once(dirname(__FILE__) . '/lib/setup.php');
// There is no php closing tag in this file,
// it is intentional because it prevents trailing whitespace problems!
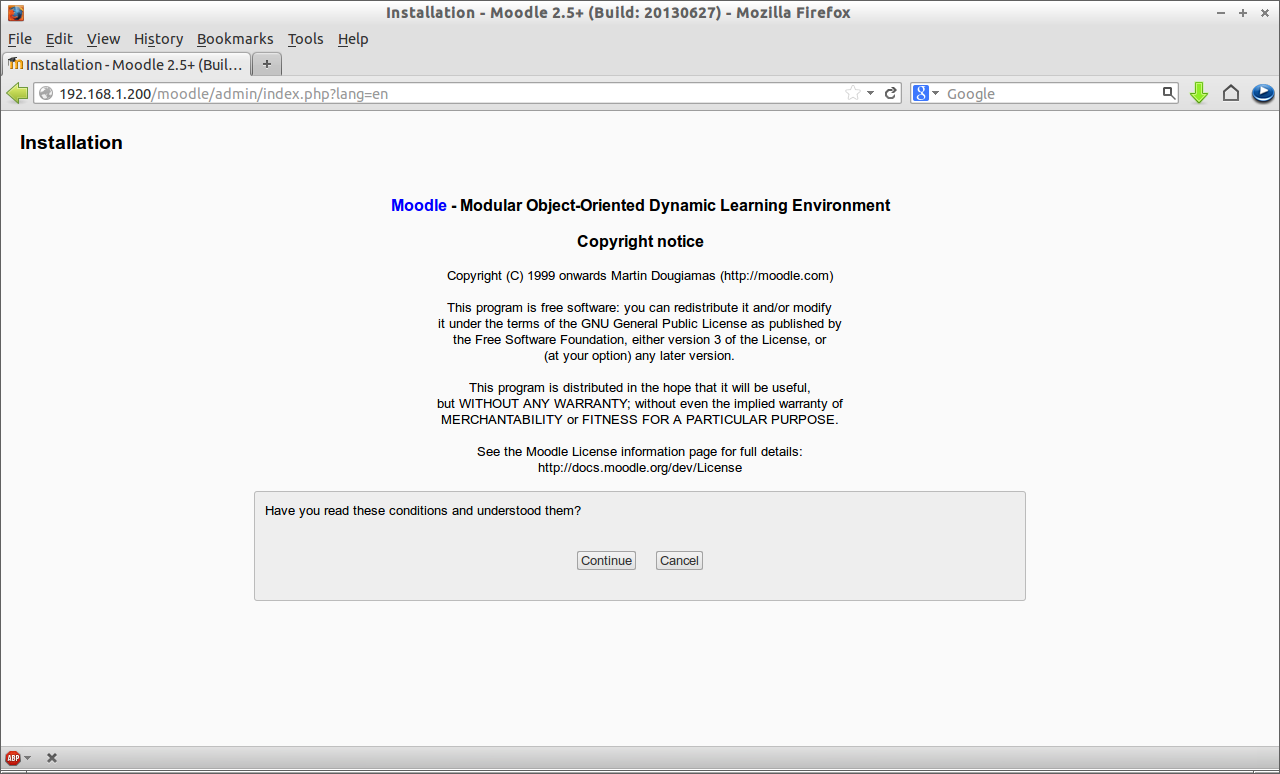
Now click Next. And click on Continue to accept the License Agreement.
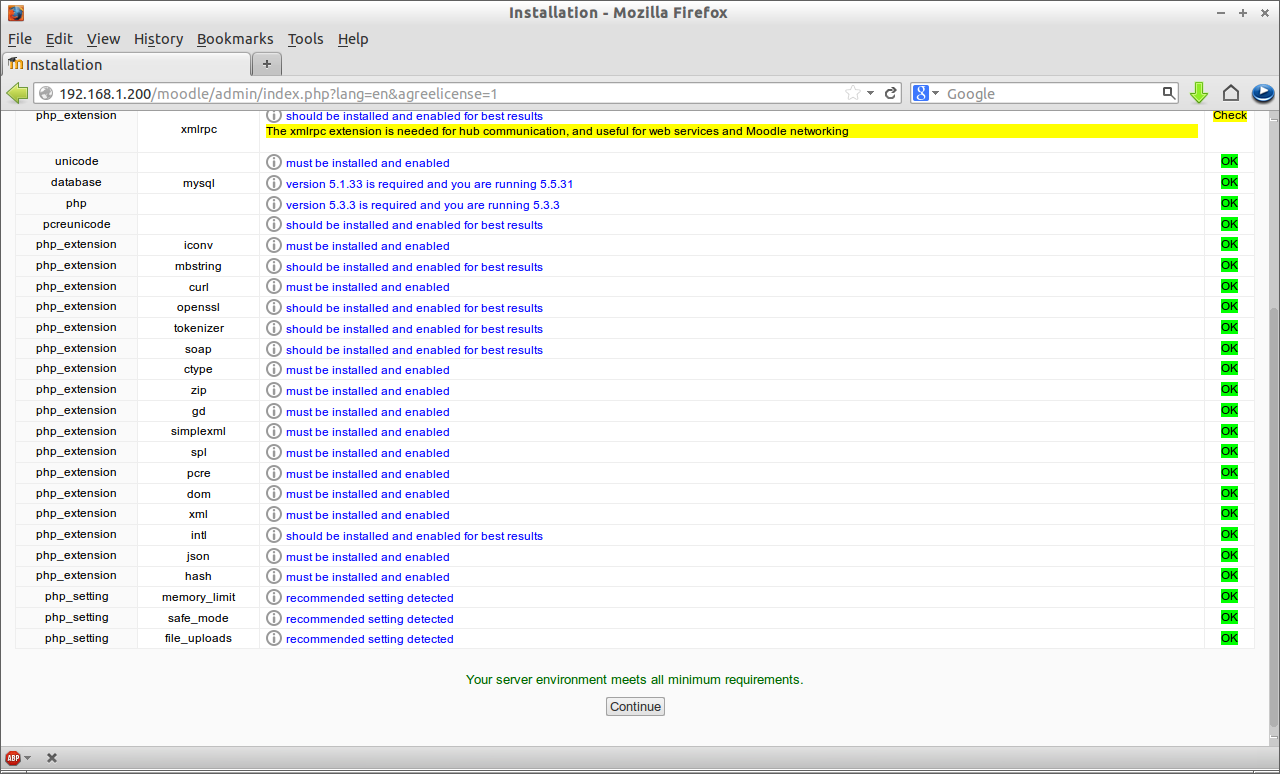
![Installation - Moodle 2.5+ (Build: 20130627) - Mozilla Firefox_007]() Now the installer will check for all necessary modules are installed. If everything seems OK, press Continue.
Now the installer will check for all necessary modules are installed. If everything seems OK, press Continue.
![Installation - Mozilla Firefox_008]() The moodle installer will create all necessary modules. This will take a while. After it completes everything, click Continue.
The moodle installer will create all necessary modules. This will take a while. After it completes everything, click Continue.
![Installation - Moodle 2.5+ (Build: 20130627) - Mozilla Firefox_009]() Create a Administrator account and click Update.
Create a Administrator account and click Update.
![Installation - Mozilla Firefox_010]() Enter the Site name and click Save Changes button.
Enter the Site name and click Save Changes button.
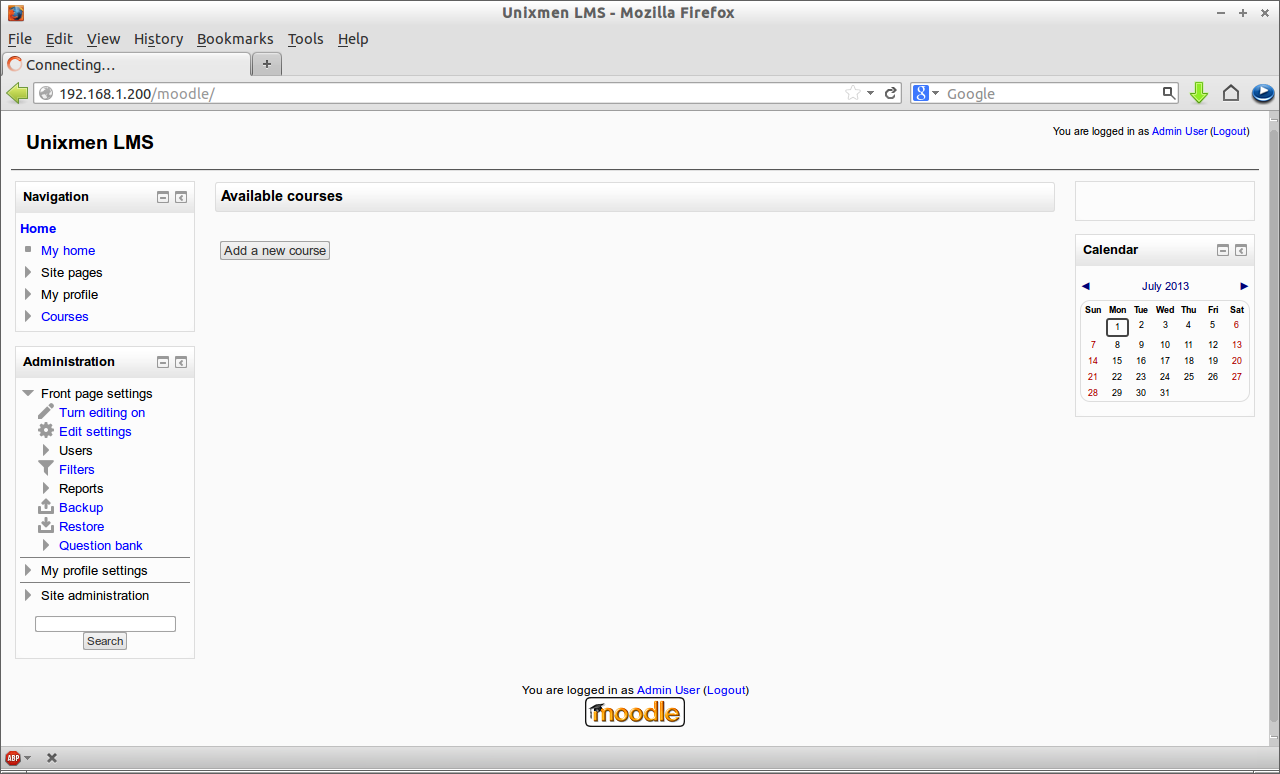
![Unixmen LMS - Mozilla Firefox_012]() Now your moodle site has been successfully installed.
Now your moodle site has been successfully installed.
Setup cron for Moodle
It is very important to setup Cron. The Moodle ‘cron’ process is a PHP script that must be run regularly in the background. The Moodle cron script runs different tasks at differently scheduled intervals. The Moodle cron script runs tasks include sending mail, updating Moodle reports, RSS feeds, activity completions, posting forum messages and other tasks. Since different tasks have different schedules, not every task will run in Moodle when the cron script is triggered.
Install crontab package if it is not installed already:
[root@server ~]# yum install cronie
Now check which user is running the web server using the following command:
[root@server ~]# grep -i user /etc/httpd/conf/httpd.conf
This will display a result as shown below:
# User/Group: The name (or #number) of the user/group to run httpd as.
# . On SCO (ODT 3) use "User nouser" and "Group nogroup".
# suggested workaround is to create a user www and use that user.
User apache
# UserDir: The name of the directory that is appended onto a user's home
# directory if a ~user request is received.
# The path to the end user account 'public_html' directory must be
# accessible to the webserver userid. This usually means that ~userid
# must have permissions of 711, ~userid/public_html must have permissions
<IfModule mod_userdir.c>
# UserDir is disabled by default since it can confirm the presence
# of a username on the system (depending on home directory
UserDir disabled
# To enable requests to /~user/ to serve the user's public_html
# directory, remove the "UserDir disabled" line above, and uncomment
#UserDir public_html
# Control access to UserDir directories. The following is an example
LogFormat "%h %l %u %t \"%r\" %>s %b \"%{Referer}i\" \"%{User-Agent}i\"" combined
LogFormat "%{User-agent}i" agent
#LogFormat "%h %l %u %t \"%r\" %>s %b \"%{Referer}i\" \"%{User-Agent}i\" %I %O" combinedio
From the above result, apache user is running the web server. So let us set the cron job for apache user:
[root@server ~]# crontab -u apache -e
Add the followong line:
*/15 * * * * /usr/bin/php /var/www/html/moodle/admin/cli/cron.php
The above command will run cron job every 15 minutes intervals on all day. Make sure that you have replaced with your own moodle path. Save and exit the file.
Go through the Moodle documentation page to know more about Moodle installation and administration.
---------------------------------------------------------------------
Install Moodle Learning Managment System on CentOS 6